Man-in-the-middle attacks
Project attribution: Project done in collaboration with Teodor Lungu.
Source: The project’s source code is available here.
Short description: Python app that executes standard man-in-the-middle attacks: ARP table poisoning, DNS spoofing and TCP Telnet session hijackin.
Technologies: Python, Tkinter, Scapy.
What I did: I implemented the GUI and the ARP and DNS attacks, but also helped around with polishing the TCP hijacking.
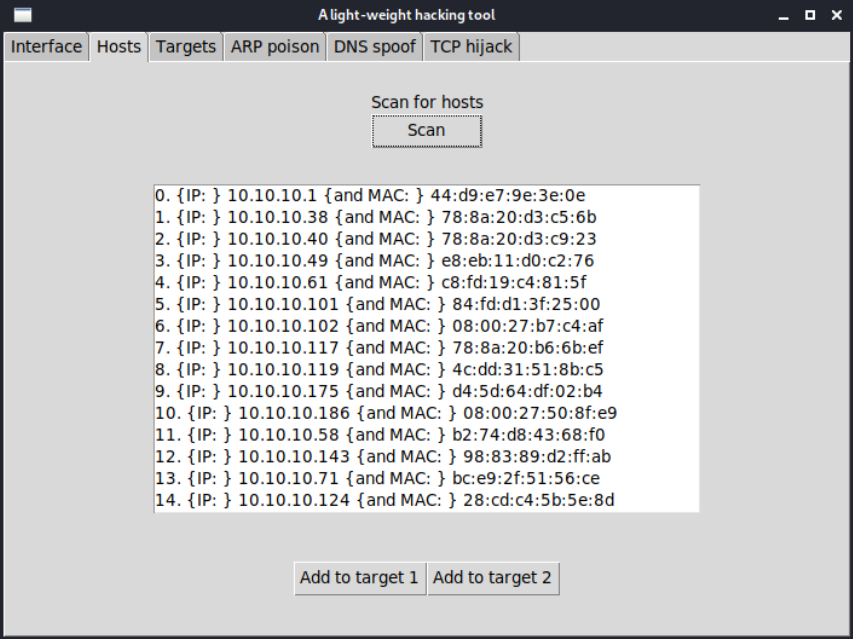
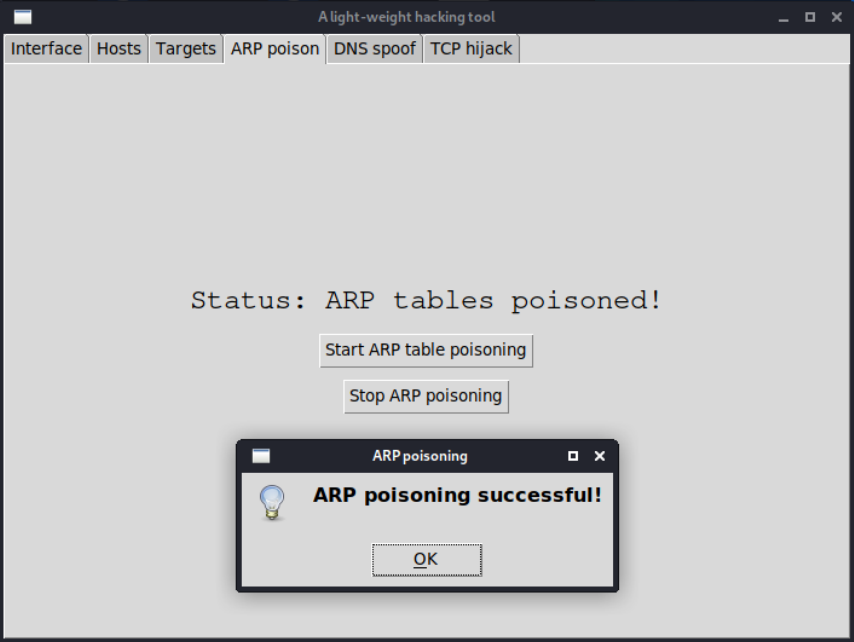
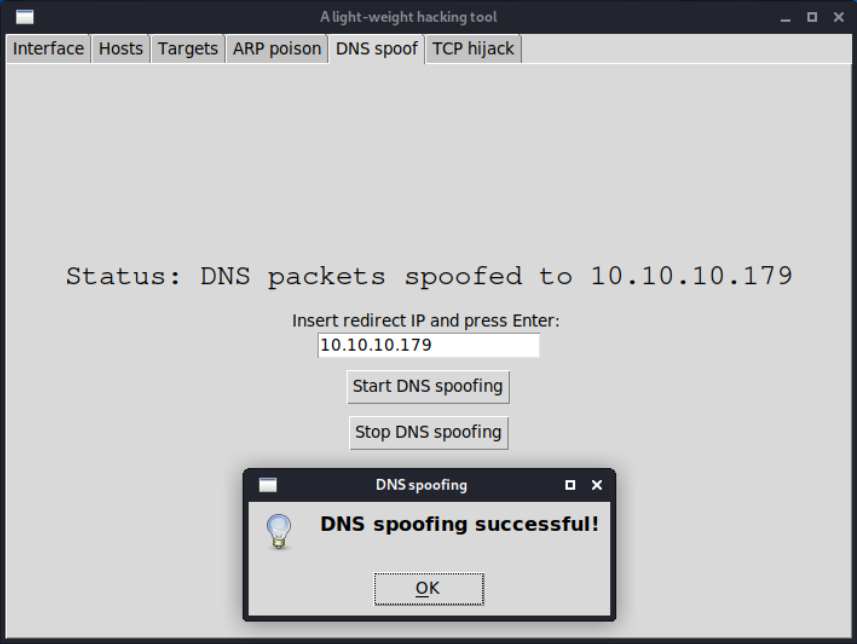
We designed and implemented a lightweight tool in Python using the Scapy network packets manipulation library, for 3 network attacks: ARP table poisoning, DNS spoofing and TCP Telnet session hijacking. I also implemented a GUI with the Tkinter library for ease of use.